The third mitigation strategy, Configure Microsoft Office Macro Settings, is designed to effectively manage the risk of allowing macros in an organisation’s environment.
As Microsoft Office applications can execute code (known as a macro) to automate routine tasks inside of office documents like Word, Excel and PowerPoint, Microsoft Office macros are a common initial vector for an attacker to gain access to an organisation’s network.
When it comes to the remediation strategy, organisations should consider simply disabling all use of Microsoft Office macros. This simple, cost-effective mitigation, when paired with an appropriate level of logging, allows an organisation to reach up to Maturity Level Three of the framework for this strategy. If your organisation does require the use of macro’s, the full set of controls must be considered.
The different approaches for macro configuration
The ACSC has developed an overview to display the “security benefit, business impact and implementation difficulty of different approaches to managing macros in Microsoft Office files.”
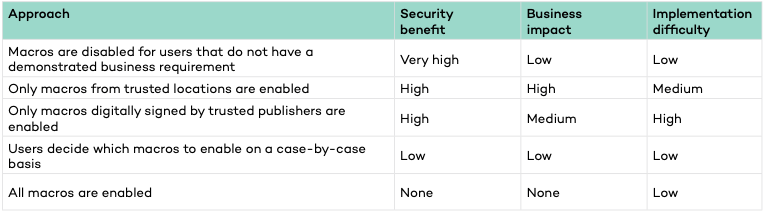
Determining which macros to trust
If there is an organisation requirement to utilise macros that cannot reasonably be replaced with safer technology, the full set of controls to authorise Microsoft Office macros and harden the Office applications will need to be considered. The ACSC recommends all macros created by users and third parties be reviewed and assessed to be safe before being approved for use within an organisation. To do so, organisations must ask themselves the following recommended questions:
- Is there a business requirement for a particular macro?
- Has the macro been developed or provided by a trusted party?
- Has the macro been validated by a trustworthy and technically skilled party?
REMEDIATION STRATEGIES
Maturity Level One
Maturity Level One organisations must ensure Microsoft Office macros are disabled for users that do not have a demonstrated business requirement, block Microsoft Office macros in files originating from the internet, enable Microsoft Office macro antivirus scanning, and ensure macro security settings cannot be changed by users.
Maturity Level Two
Maturity Level Two organisations expand their strategy to implement Windows Defender Attack Surface Reduction (ASR) rules to prevent Microsoft Office macros from making Win32 API calls and establish a technical policy to enable logging of allowed and blocked Microsoft Office macro executions.
Maturity Level Three
At Maturity Level Three, organisations configure trusted locations and provide training in the use of trusted location to internal staff with competency to review Macro code and authorise new macro code for the organisation.
Organisations need to restrict write access to trusted locations to just those users with sufficient training and expertise to recognise malicious code, and ensure these users are aware that they have a responsibility to do so before placing a document in a trusted location.
Maturity Level Three, organisations must block macros from known untrusted publishers from use even for authorised users or trusted locations, establish and commit to an annual process to inspect Microsoft Office’s list of trusted publishers and ensure that their membership on this list is appropriate. Organisations must also ensure logging of macro use established under Maturity Level Two is forwarded to a Security Information and Event Management (SIEM) system to monitor for the unauthorised use of Microsoft Office macros, signs of compromise, and ensure that event detections are monitored and acted on.
