One of the challenges when managing workloads on cloud services is managing them in a secure way. This is especially true when you manage virtual machines you do not want to expose.
Accessing and managing virtual machines in an on-premises environment is usually done either using Remote Desktop Protocol (RDP) for Windows machines or Secure Shell (SSH) for Linux machines.
Accessing such virtual machines in on-premises environments is usually secure because you can not connect to them unless you are connected to the corporate network and the corresponding communication ports (22 for SSH and 3389 for RDP) are (usually) blocked from the internet.
That said, when your virtual machines are running as cloud services, this becomes more challenging as these virtual machines are no longer secured by hosting within the closed corporate network but on the virtual network running on the cloud service. This results in management ports needing to be opened on the internet, posing a big security issue as these ports are well known and continuously scanned by threat actors trying to gain access and control to unsecured workloads
(you can read this article applying to AWS here.
On the Microsoft cloud computing platform, Microsoft Azure, when you set up and/or are running virtual machines, you have a notification when you open inbound communication to your virtual machine using any of the management ports (22 or 3389).
Well, what are my options to be able to manage my virtual machines on Azure in a secure way?
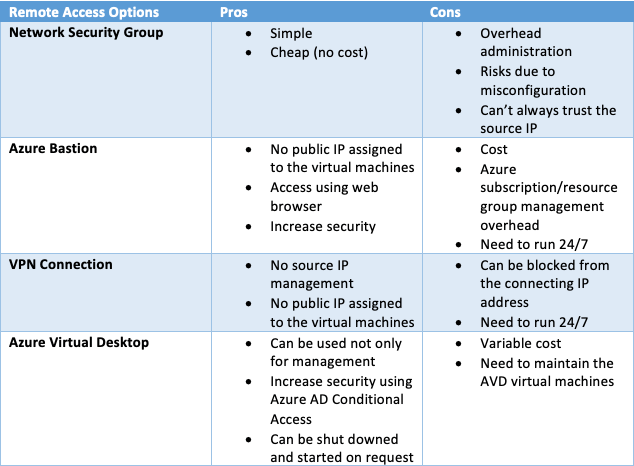
Luckily you have quite few options, each of the with their pros and cons – either cost or administrative overhead. To secure management access to virtual machines running in Azure you have the below options:
- Configure Network Security Group (NSG) to allow access from specific IP’s on these management ports
- Azure Bastion, a feature which allows you to connect to your virtual machines using the management ports from the web browser
- VPN connections which tunnel the management traffic through a Virtual Private Network
- Azure Virtual Desktop which allows you to access a Windows virtual desktop which then will let you connect to your virtual machines using any of the management protocols
So, let’s have a detailed look at these options.
Use Network Security Group rules
Implementing NSG to manage inbound management traffic is probably the simplest and most cost-effective solution.
You can configure an inbound rule to allow management protocols to your virtual machines from only specific IP’s.
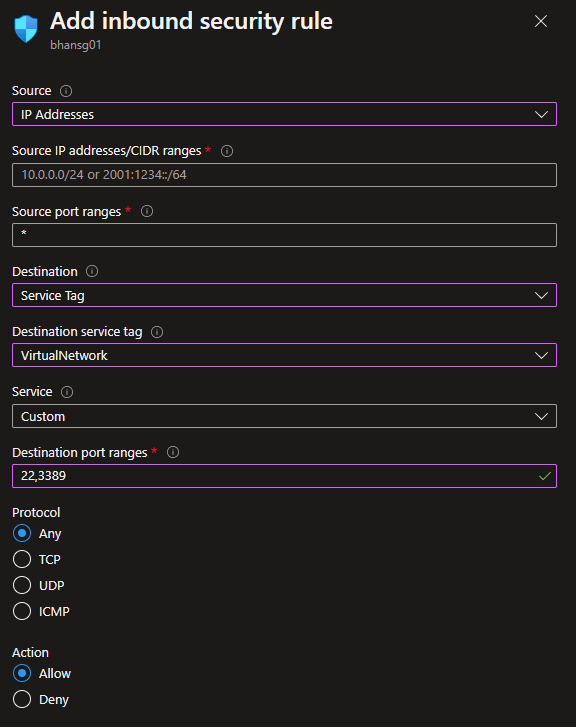
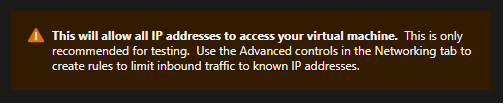
While it sounds clear and simple, this introduces an administration overhead and potential security concern as each virtual machine will need to have a public IP address (which also adds more cost) assigned to them. Indeed, in a modern workspace world, people (which includes your administrators but also potentially your users and partners) can work from anywhere. This means the source IP addresses may be difficult to track, especially when working from home (which is part of the norm now).
Using NSG rules to allow inbound management traffic may sound like a cheap (there is not cost associated with NSG’s) and easy way but you will need to, one way or another, provide the ability to update the source IP addresses to anybody who needs to manage your virtual machine.
This can quickly become a nightmare to manage and maintain.
Network Security Groups are a very well-known and simple way to secure traffic (inbound or outbound) from an Azure Virtual Network, but any uncontrolled change or misconfiguration may put you at risk.
Plus, you are not able to implement additional security layers, such as requesting Multi Factor Authentication, and home IP addresses may change, which means you can trust one IP address at one point of time but then the same IP address is being assigned to a rogue device which puts you at even more risk.
Azure Bastion
Azure Bastion is a specific capability of Microsoft Azure which allows you to connect to your virtual machines for management purposes directly from the web browser.
The principal benefit of Azure Bastion is all of your virtual machines do not need any more public IP addresses associated with them and you don’t need to manage NSG inbound security inbound rule.
The downsides of Azure Bastion are the cost (starting at 0.19 USD per hour plus outbound traffic over 5Gb per month and it must be running 24/7) and you need to grant access to your Azure subscription/resource group to allow the user to access the virtual machine from the web browser.
Indeed, because Azure Bastion allows you to remotely connect to the virtual machine through the web browser you need to allow the user managing the VM to connect and access the VM from the Azure portal.